Welcome to the 21st installment of “OT Hunt” where we dive into the challenges and opportunities within the realm of ICS/OT devices connected to the internet. This series aims to raise awareness among asset owners and ICS vendors, encouraging them to proactively secure their infrastructures.
The Discovery: T5 PLCs on the Internet
One day, I was exploring ZoomEye using the query device:"plc", searching for new PLC brands or types. To my surprise, a more refined search with the filter device:"plc" +app:"T5" revealed almost 2,500 online T5 PLC devices. These were predominantly located in Italy, with smaller distributions across other countries.
This discovery piqued my curiosity. What exactly is the T5 PLC? After some digging, I found that it originates from a French vendor, COPALP (now COPA-DATA France), which specializes in industrial products like historian and PLCs. Learn more about them at COPA-DATA.
Observations on Security: The Weak Links
Unfortunately, my findings revealed significant security lapses, particularly in China, where many T5 PLCs were exposed with weak configurations. Here’s what stood out:
1. Open FTP Ports with Anonymous Login
- Several hosts had FTP ports open with anonymous login enabled, granting unauthorized users access to files and data.
2. Open Telnet Ports
- The presence of open Telnet ports further amplified the risks, as attackers could potentially gain control over the devices using plaintext credentials.
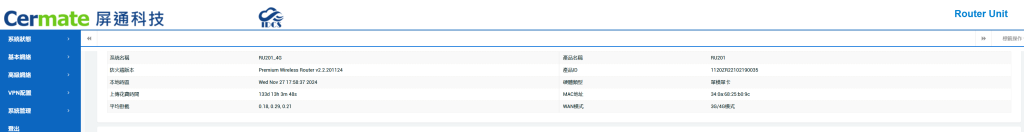
3. Vulnerable Cermate Routers
- Many of these devices were connected via Cermate routers, which act as HMI gateways to the internet. Shockingly, most of these routers had their web management interfaces exposed with default credentials (
admin/admin), leaving them wide open to attackers.
4. RTSP Ports (554) Exposed
- The Real-Time Streaming Protocol (RTSP) was also commonly exposed. RTSP is used for controlling streaming media servers but, when misconfigured, can increase the attack surface dramatically.
The Risks of Exposed RTSP Ports:
- Discover Internal Camera Streams: Attackers can access internal camera feeds.
- HMI Access: Some HMIs receive data from cameras, creating an indirect pathway to the ICS network.
- Pivoting into ICS Networks: Exploiting RTSP can provide a foothold for lateral movement.
- URL Brute Force Attacks: Attackers can discover stream URLs via brute force.
- Credential Brute Force Attacks: Tools like Hydra can be used to brute force RTSP credentials.
Testing RTSP Configurations: Tools and Techniques
If you’re dealing with RTSP exposure, testing its configuration can help identify vulnerabilities. Here are some tools and methods to try:
1. curl Command
curl -i -X DESCRIBE rtsp://10.10.14.30/Streaming/Channels/101
- This command reveals details about the media being streamed.
2. nmap with RTSP Scripts
nmap -sV --script "rtsp-*" -p 554 10.10.14.30
- Useful for finding:
- RTSP server version
- Available streams and channel URLs
- Supported RTSP methods
3. Hydra Brute Force
hydra -s 554 -l admin -P /path/to/wordlist.txt rtsp://10.10.14.30
- Discovers media/channel paths using brute force with wordlists.
4. VLC for Stream Viewing
vlc rtsp://10.10.14.30/live
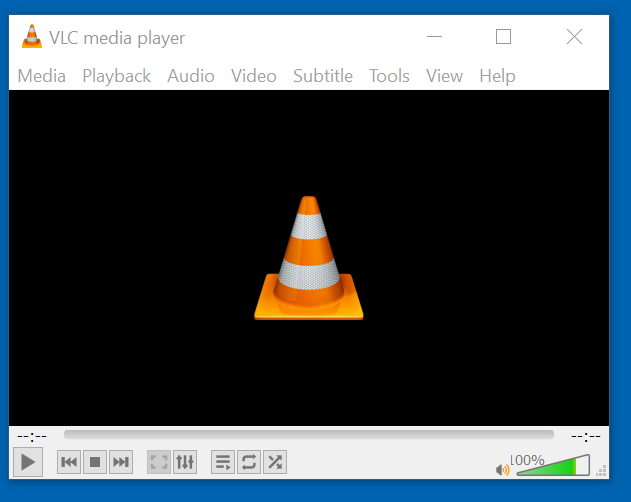
- Open unauthenticated streams in VLC to view media. This could expose facility videos and images, providing attackers with critical insights.
Summary: The Cost of Exposure
When industrial devices like PLCs are exposed to the internet, the risks are high. My research found that many T5 PLCs also had open Modbus ports (502), which attackers could exploit using open-source tools to pull data. Combining this with vulnerable services like FTP, Telnet, and RTSP creates multiple entry points for attackers.
The critical question is: Who knows what’s behind these exposed devices?
Conclusion: Stay Vigilant
This article highlights critical security vulnerabilities in T5 Programmable Logic Controllers (PLCs) and routers utilizing the Real-Time Streaming Protocol (RTSP).These weaknesses can be exploited by cyber criminals to disrupt industrial control systems, leading to potential operational failures and safety hazards. The article underscores the importance of implementing robust security measures, such as regular firmware updates, network segmentation, and stringent access controls, to safeguard these systems against cyber threats.
ICSRank is here to help you discover, assess, and secure your ICS/OT systems. Stay tuned for more insights in future OT Hunt installments. Together, we can defend critical infrastructure against evolving cyber threats.
Let’s make security a priority. Your vigilance matters.

