This is the 4th topic of “OT Hunt”. These topics expose ICS/OT devices that are connected to the internet. The goal is to build an awareness for the ICS community. This kind of research is also a warning message for asset owners and ICS/OT vendors to secure their their assets’ attack surfaces.

The following keywords/dorks I used to search for OPC on Shodan search engine, please check out my ICS dorks project at GitHub:
opc-uaThis search yielded 404 online OPC devices. The results also showed “ICS” tag for each device (based on Shodan) . Many OPC devices are linked to CodeSys software. I found 1 OPC device that interacts with profinet protocol, for example “Phoenix Contact Software PROFINET”. It connects OPC server with Profinet protocol . The results showed that some OPC servers have many open ports/surfaces such as 22 , 80 , 443 , 1883 (MQTT) , cpanel, container management , 102 (S7) , 502 (Modbus). The common port for OPC is:
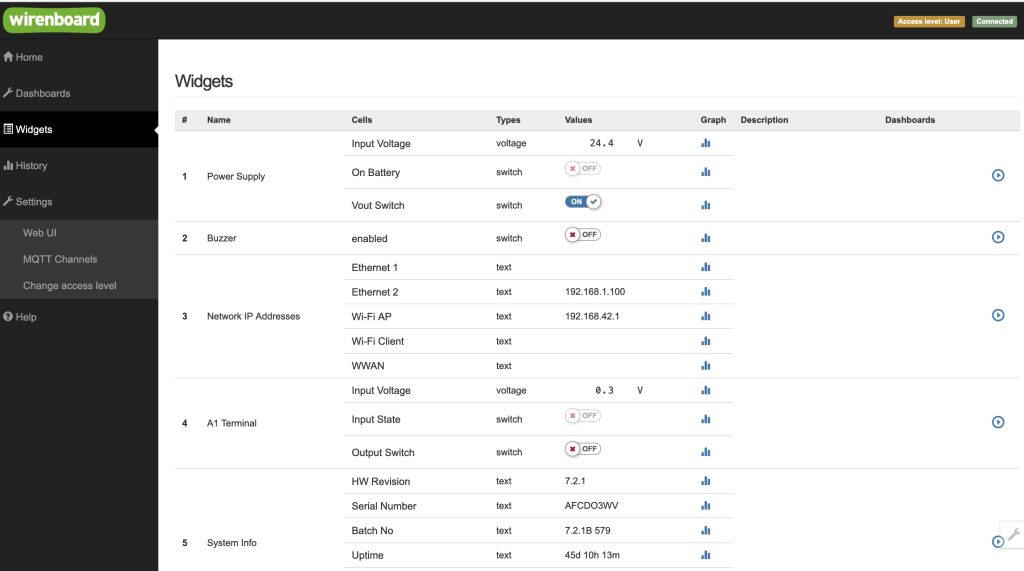
4840 TCPI found an interesting platform called “Wiren Board” its a Russian software. Its used for home and industrial automation and monitoring. Could it be liked to an OPC server in any way ? Its hosted on the same OPC machine by the way.
I also found WAGO PFC200 hosted with an OPC server . WAGO PFC200 is programmable automation controller (PAC) and is used with Codesys software , to create and run control programs, monitor and control industrial automation processes, and integrate the PFC200 into a larger automation system (source: ChatGPT). It has a web interface (attack surface !) .
http://ip-address/wbm/index.php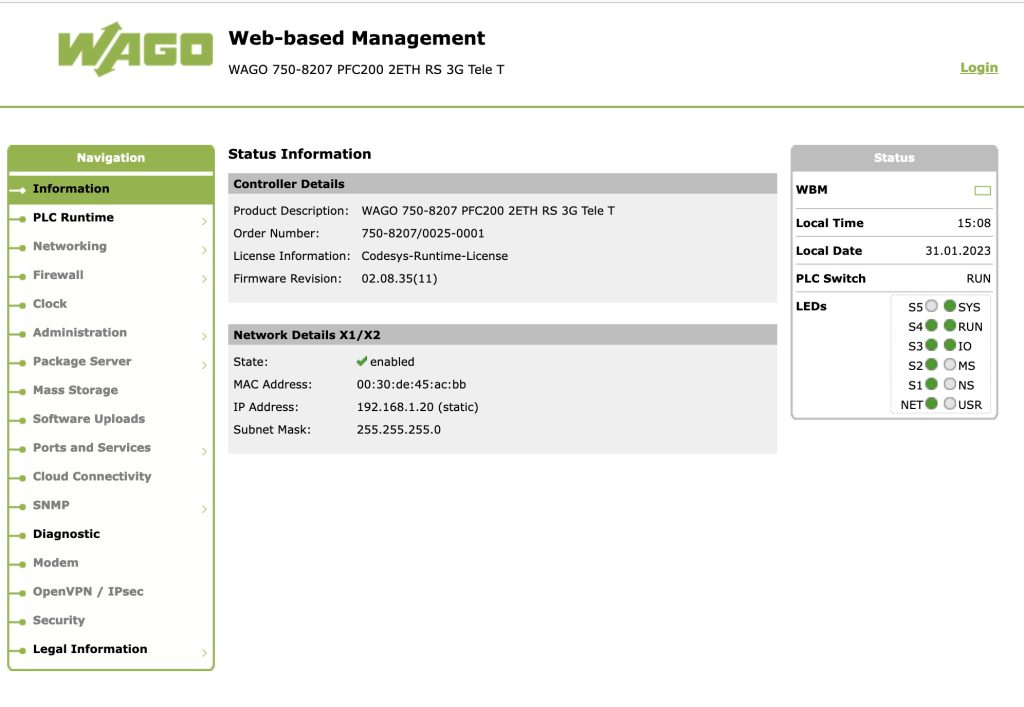
WAGO PFC200 is vulnerable and is listed on US-Cert ICS advisory. There is a risky vulnerability (Improper authentication) with a CVSS v3 score of 9.8. This vulnerability allows an attacker to change operation settings due to a vulnerability in CoDeSys Runtime application
ICSA-18-044-01Some OPC servers are hosting MQTT (iIoT ?)
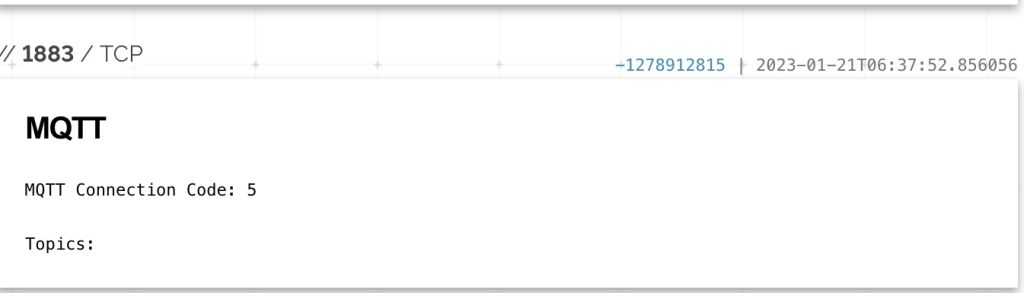
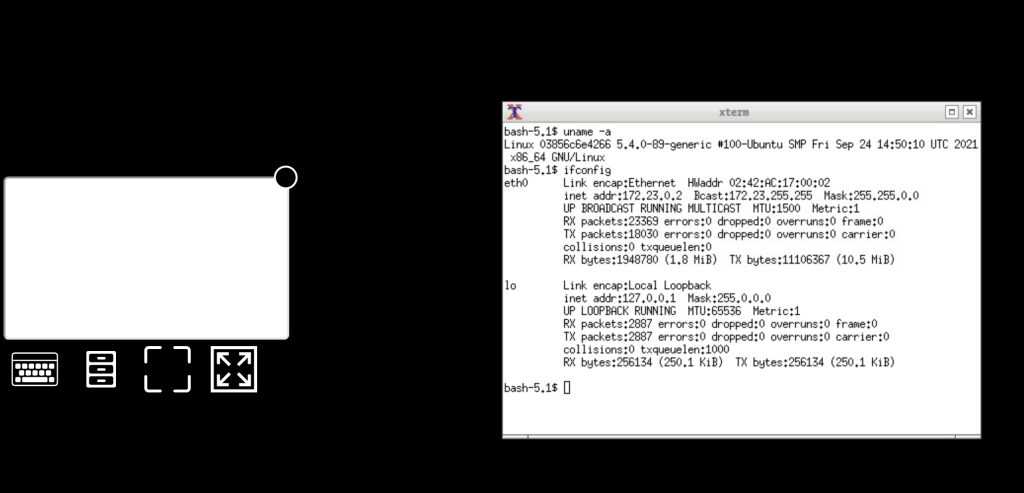
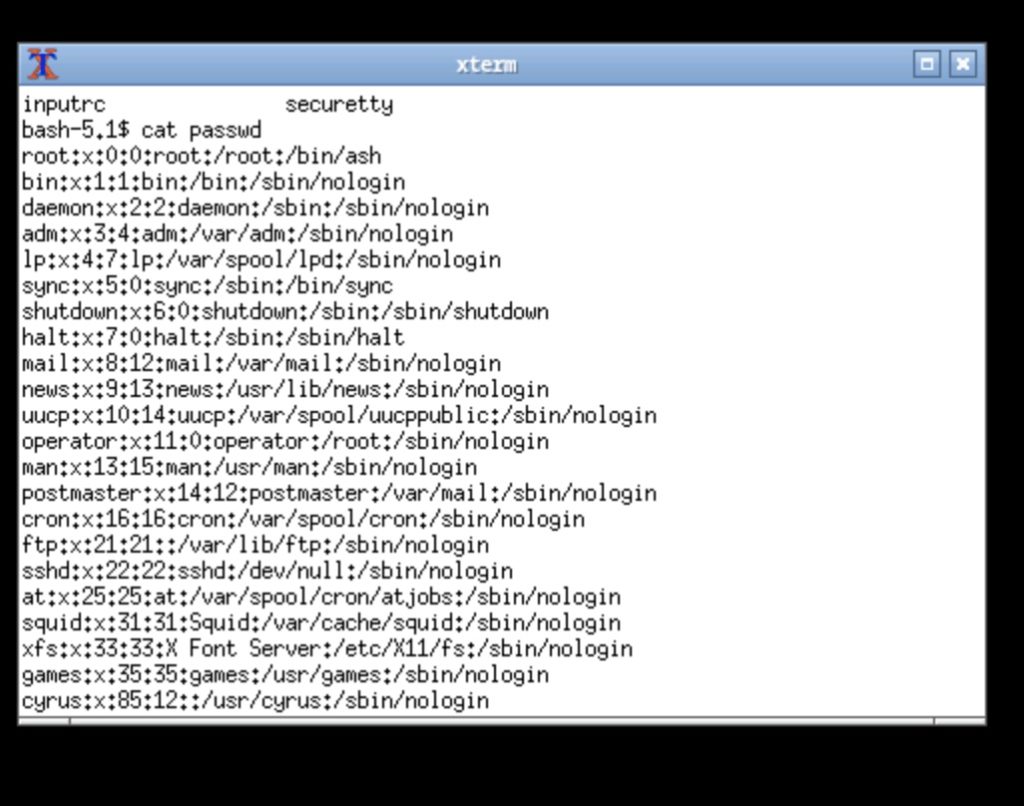
I was shocked when i saw an OPC server (ICS device) that is hosting Guacamole , this software is used to access remote desktops , the port was 1234 . I played a little with it and I managed to see the /etc/passwd file content. Use your imagination and figure out what you can accomplish with the Linux xterm command line.