This is the 6th topic of “OT Hunt”. These topics expose ICS/OT devices that are connected to the internet. The goal is to build an awareness for the ICS community. This kind of research is also a warning message for asset owners and ICS/OT vendors to secure their their assets’ attack surfaces.
In this article,I will target iIoT devices. The targeted vendor is InaHand Networks. InaHand Networks is a company that specializes in industrial IoT solutions. In this article, I will focus on routers: InRouter 615 (IR615) and InRouter 302 (IR302). InHand industrial routers are designed to enable secure and reliable connectivity for industrial applications, facilitating data exchange, monitoring, and control in industrial environments.
The following keywords/dorks I used to search for IR615 and IR302 consecutively on Shodan search engine, please check out my ICS-OT-iIoT dorks project at GitHub:
http.html:"IR615"
http.html:"IR302"The search for IR615 yielded 23 devices, most of them are located in China . There are web severs for the devices for managing settings and controlling the system. The common port for IR615 is:
8899 TCP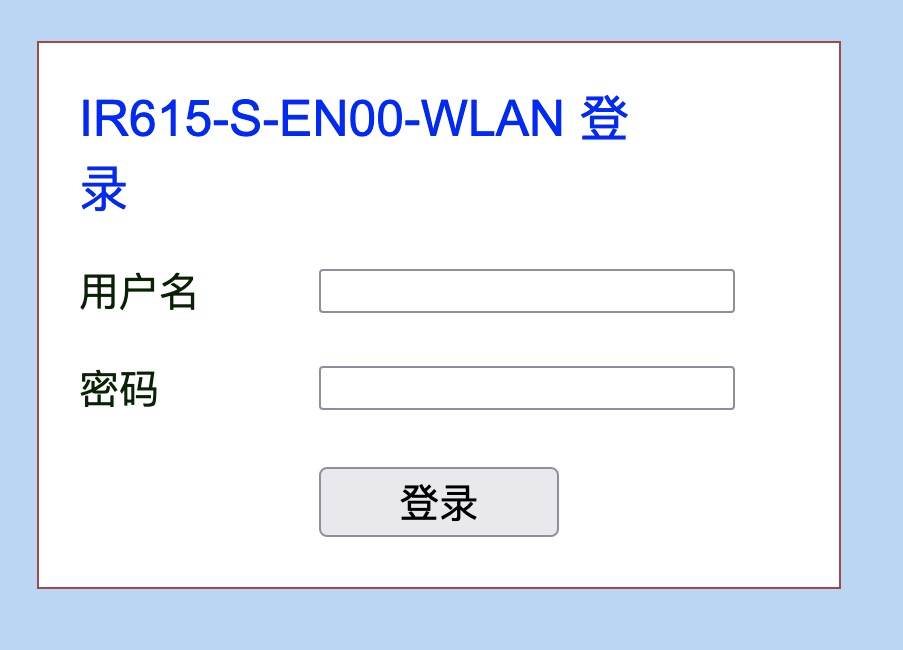
IR302 yielded 21 results. They also have web interfaces. The common port for IR302 is:
80 TCP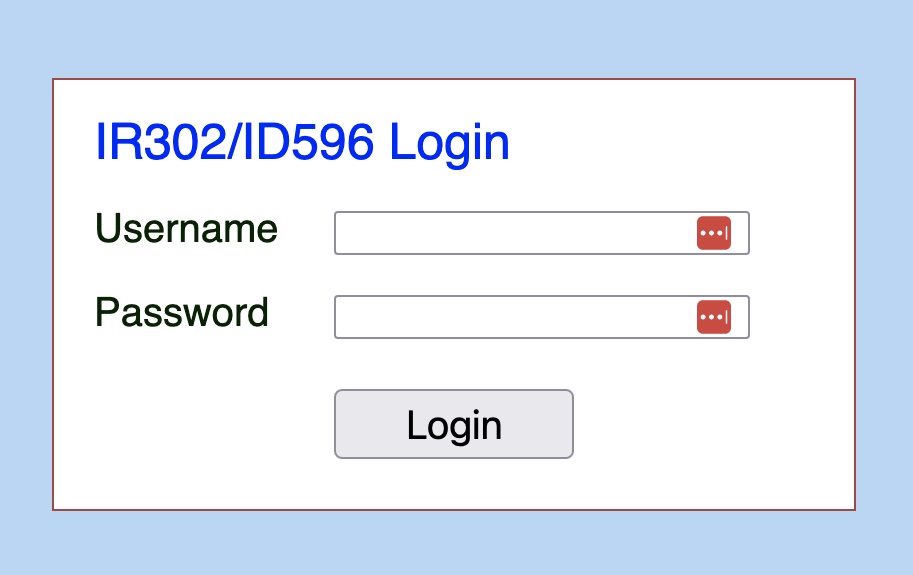
Both IR302 and IR615 suffer from security issues, their web interfaces don’t support SSL encryption. There is “no login lock” feature. They also have default credentials :
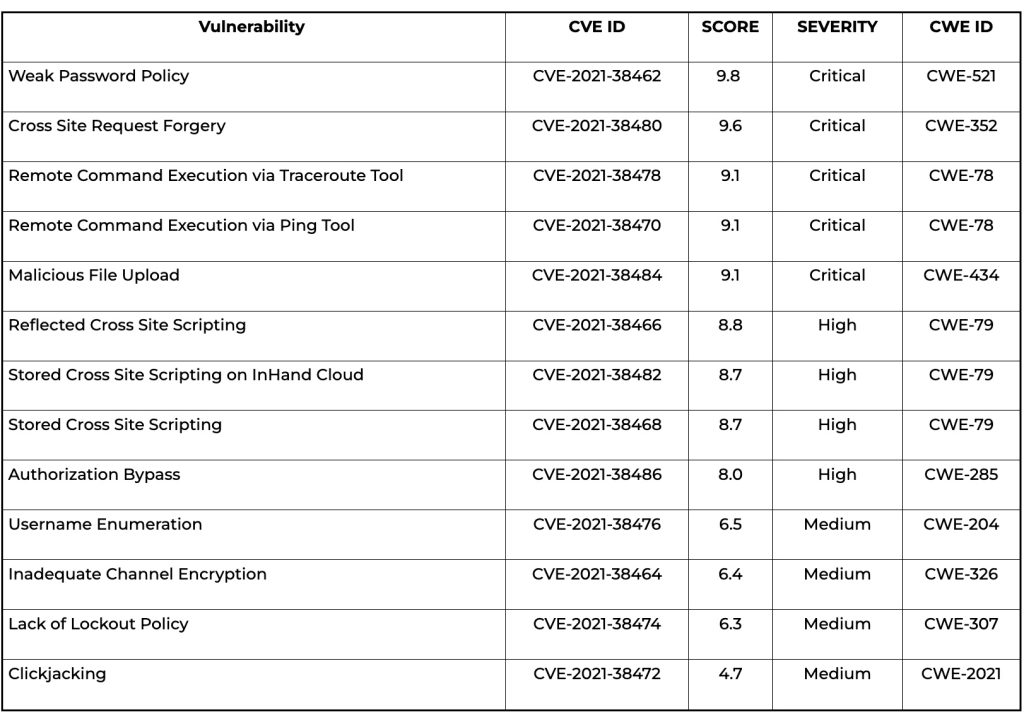
adm:123456There is a research by OTORIO that discovered 13 severe vulnerabilities in those products. An attacker can exploit InHand’s cloud-based products, which can open possibilities to reach HMIs and PLCs.